Bybit, a major cryptocurrency exchange, has released findings from its investigation into the $1.4 billion Ethereum hack that occurred on February 21, 2025, pointing to a potential compromise of Safe Global’s Amazon Web Services (AWS) S3 or CloudFront account.
The Alleged AWS Compromise
According to Ben Zhou, Bybit’s investigation was carried out by Sygnia Labs and Verichains. The cyber security firms analyzed its signers’ machines and a malicious JavaScript payload found on the Wayback Archive, suggests that Safe Global’s AWS account or API key may have been leaked or compromised. This alleged compromise allowed attackers to manipulate the Safe Wallet interface and execute a malicious contract upgrade.
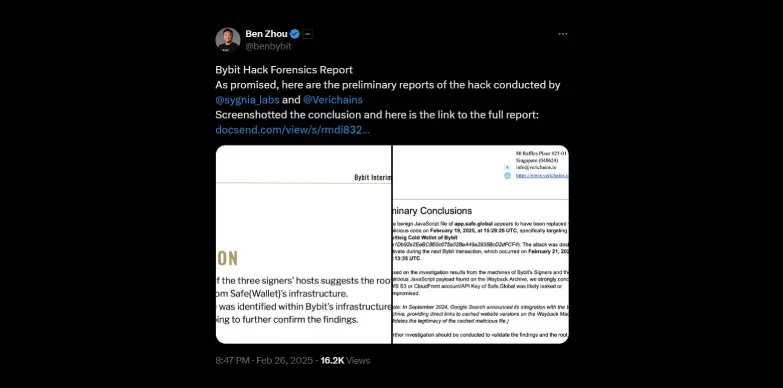
The breach, which targeted Bybit’s Ethereum cold wallet, occurred when attackers manipulated the Safe Wallet’s user interface (UI) during a routine contract upgrade.
Forensic analysis revealed that the bad actors compromised Bybit’s operators devices, displaying legitimate transaction details on-screen while secretly executing a hostile contract upgrade. This allowed the theft of 446,870 ETH (1.4 billion) before detection.
CertiK’s technical analysis supports the claim that multiple developer devices were compromised, which allowed the attackers to manipulate the Safe wallet front-end to display a legitimate transaction data while sending a malicious data to the ledger for signing.
Bybit’s Response and Asset Backing
As Ben Zhou explained in Wu Blockchain Podcast, the signer just saw a masked UI displaying the correct address and the correct transaction data, but it was altered when sent to the Ledger for signing.
Despite this breach, the cryptocurrency exchange made sure that they maintain transparency with its users. A third party audit by Hacken confirmed Bybit’s current reserves and according to the CEO of Bybit, the exchange has fully closed the ETH gap and is back to 100% 1:1 on client assets through Merkle tree verification.
Also Read: Bitcoin Won’t Die: CZ’s Reassuring Words Amid Crypto Crash

